INHOME
How secure is your home network?
Technological hardware and software advancements in personal computing, communications, networking devices, and their infrastructure have provided the base for widespread adoption of in-home WiFi networks that enable work from home, distance learning, and online financial transactions. In parallel, insecure networked devices, IoTs, have become more common in homes. Cameras, personal assistants, and medical devices are examples of such devices commonly used in a home network. The use of home networks and the number of IoT devices on them is predicted to continue to grow but IoT devices typically lack strong and effective cybersecurity putting end users and others at increased risk of cyber attacks. Many of these IoTs are connected on the same home WiFi network along with other privacy and security sensitive devices like personal and business laptops, phones, and printers in many cases without even network segmentation keeping them separate. This makes accessing corporate assets from home, transferring sensitive medical data, and conducting financial transactions on home networks at higher risk of cyber attack. With the increased number of devices, users, and volumes of unprotected data, the risk and probability of cybersecurity attacks also increases. IoT devices and commercially available home network solutions are not available that can provide strong cybersecurity protection and reduce the potential of attack. Additionally, end users may be unaware of the threats and do not understand how best to protect themselves.
Reduce your probability of cyber attack
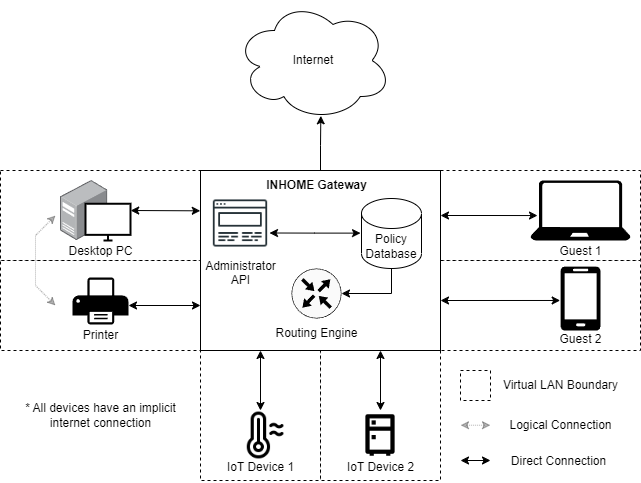
There is an absence of well defined and widely accepted cybersecurity standards for IoTs; they typically lack the resources required for strong cybersecurity and manufacturers are not incentivized to support it. However, there is an opportunity to close this gap. Zero Trust Architecture (ZTA) is a leading standard for secure networks however, no such solutions are currently available for home networks. Through the use of INHOME's unique device and access policy management forcing device network segmentation and strong cryptographic inter-device packet authentication, IoT devices can be made to adhere to several critical ZTA principles. The result is home network owners, their families, and other end users can be better protected from cyber attacks. With INHOME, homes can be safer, more reliable, and available for critical needs like remote work, health monitoring, and conducting online financial transactions.
Enjoy and benefit from strong cybersecurity of your home network through INHOME zero trust architecture based protection.
FAQs
- Q> Why isn't using my home router's guest network support sufficient protection?
- A> Using your home router's out of the box guest network support is a good first step. However, as all devices in the guest network have the potential to communicate with each other, there is no strong standards based encrypted authentication and authorization of traffic between any devices leaving the potential for spoofing and other cyber attacks.
- Q> I see other home network solutions promising cybersecurity protection. What does your solution offer that they do not?
- A> Those solutions make it harder for attackers to gain a foothold in home networks, but none of them prevent lateral movement once an attacker enters the network. INHOME offers such protection through Zero Trust principles such as secure cryptographic communications between devices and default network segmentation.
- Q> How does INHOME improve upon out-of-the box guest network segmentation?
- A> Through the use of a gateway and strong standard's based cryptographic packet authentication, INHOME guarantees that a device added to the network will by default only be able to access the external internet through an ISP provider unless authorized through access control policies to communicate with other devices where every packet transferred between two devices is authenticated.
- Q> Isn’t this complicated to set up and maintain?
- A> INHOME has an easy to use admin interface for defining and managing access policies and for adding, renaming, and removing devices.
Future Enhancements
- IPv6 support
- Automated device discovery and point and click device and policy management
- Multiple administrative domains
- Device metrics dashboards
- Anomaly detection through device and traffic flow profiling
- Automated alerting and device quarantining
- Multi-factor authentication for the administrative interface