CybersecStandards: Cybersecurity Guidance for COVID-19 Pandemic Tracking
Our Project
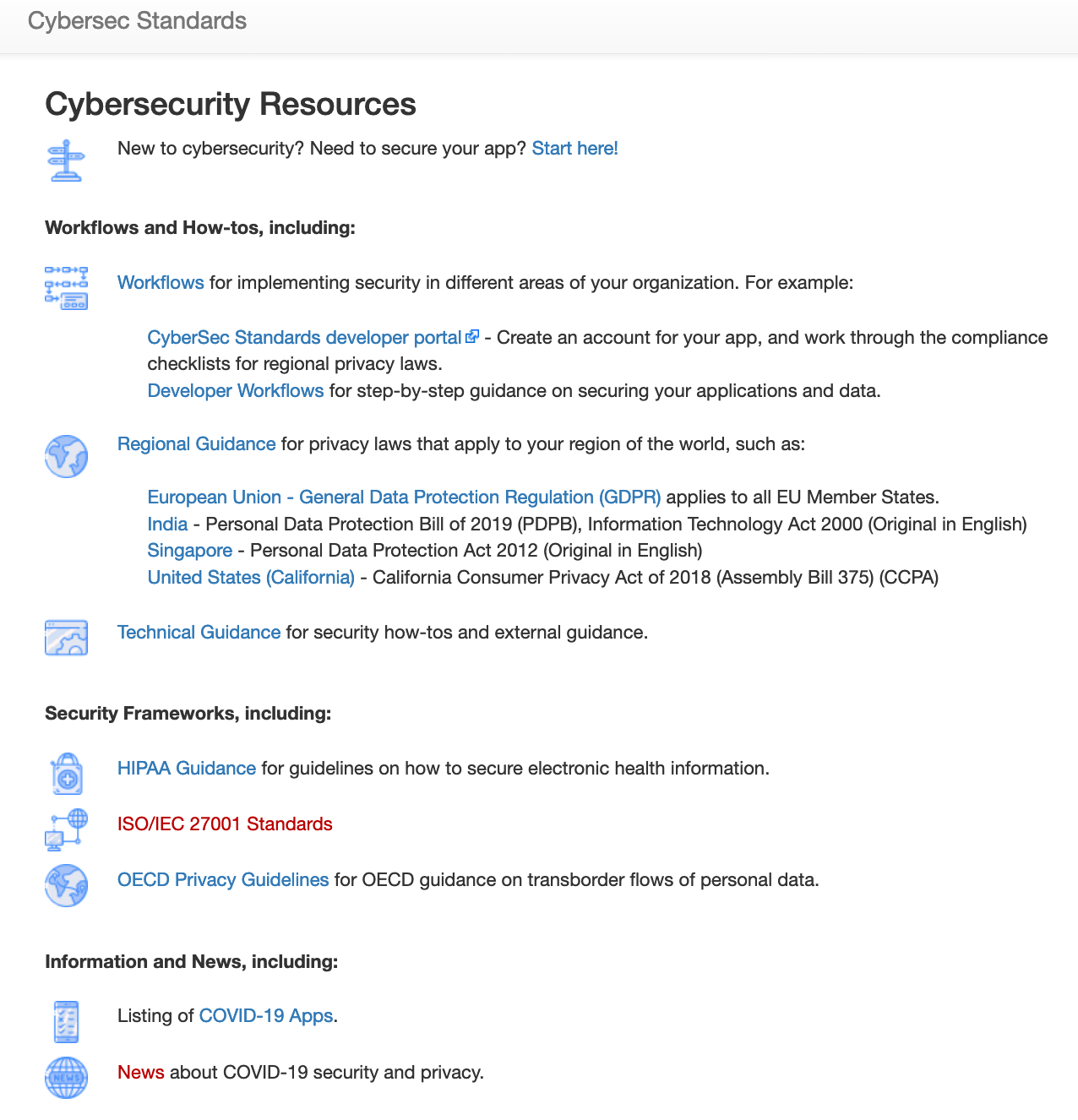
A unified cybersecurity framework/repository that provides guidance for pandemic response technologies at different stages of the epidemiological management lifecycle. It incorporates technical guidance, compliance requirements (regulatory requirements, privacy law etc.) and industry- and location-specific guidance.
Why
Internationally, there are multiple independent tech-based efforts to respond to the COVID-19 pandemic. Some implementations present significant risk exposure due to a lack of security controls. Some of the technical implementations include multiple independent implementations of insecure mobile apps for contact tracing, and multiple jurisdictions publicizing inadequately-anonymized infection and mortality data.
At a later stage in the epidemiological management model, other tech-based solutions may emerge, such as wearable tech to monitor users' health. These will also require security guidance.
Who
Many of the participants who are building solutions in this ecosystem may not be experienced in integrating security into their solutions, which likely also prioritize the urgency of immediate functionality over a lengthier formal development process.
However, there is no unified, easily-understandable cybersecurity framework that governs the data security or the network security that should be utilized by these disparate technological responses. Easily-accessible guidance is critical in a response that requires international coordination and interoperability.
Potentially, an inability to demonstrate adequate security and privacy protection may inhibit adoption of these tech-based solutions or data publications.
Our project provides guidance for these developers to build secure solutions, and possibly meet compliance requirements where applicable. Our framework/repository is available for anyone who needs guidance to implement their solutions securely. E.g. app developers, data publishers, network infrastructure engineers.
What
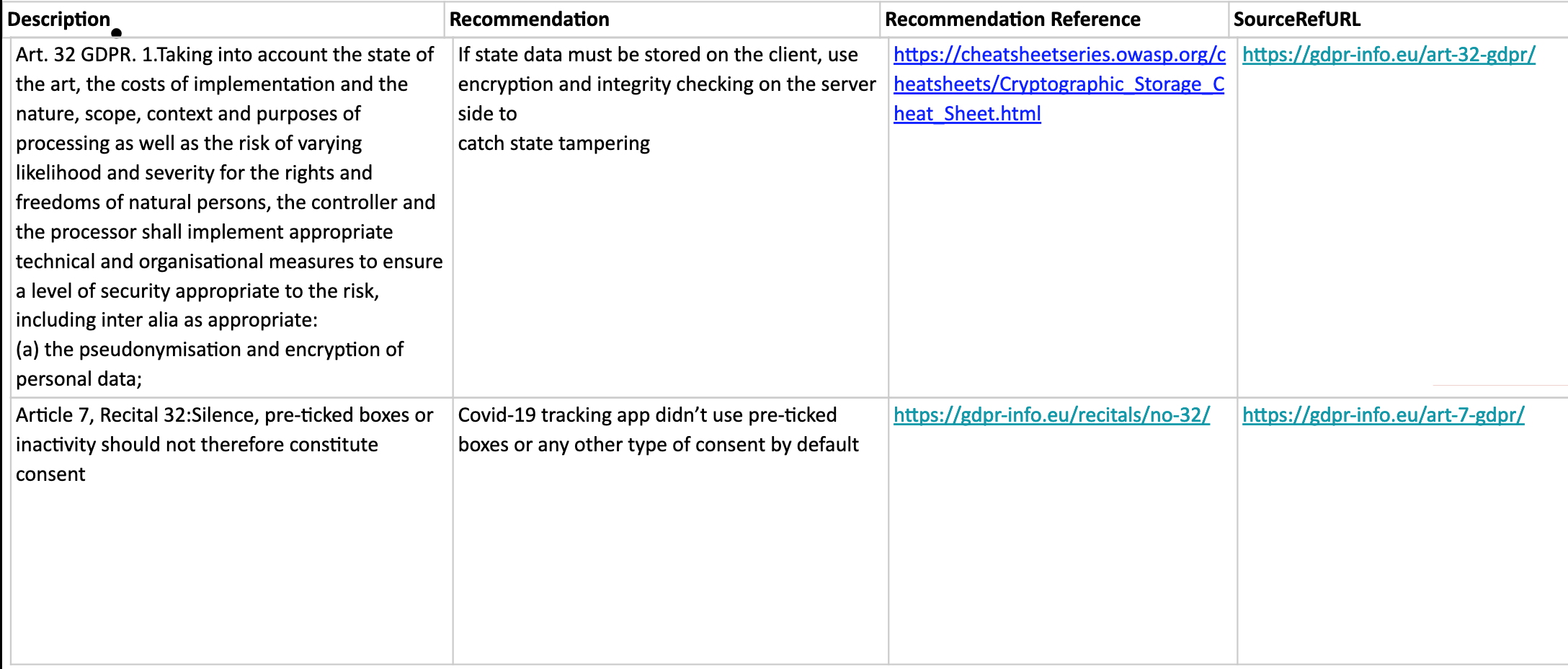
We reviewed the data security and privacy requirements for each region. We then categorized them by their various types, i.e. technical controls, governance controls, data processing controls, etc. For each of these types, we mapped an action to each requirement by providing a recommended solution, together with an implementation reference from external sources (for e.g. OWASP Cheat Sheet Series, Recitals of the GDPR, Medium articles, etc.)
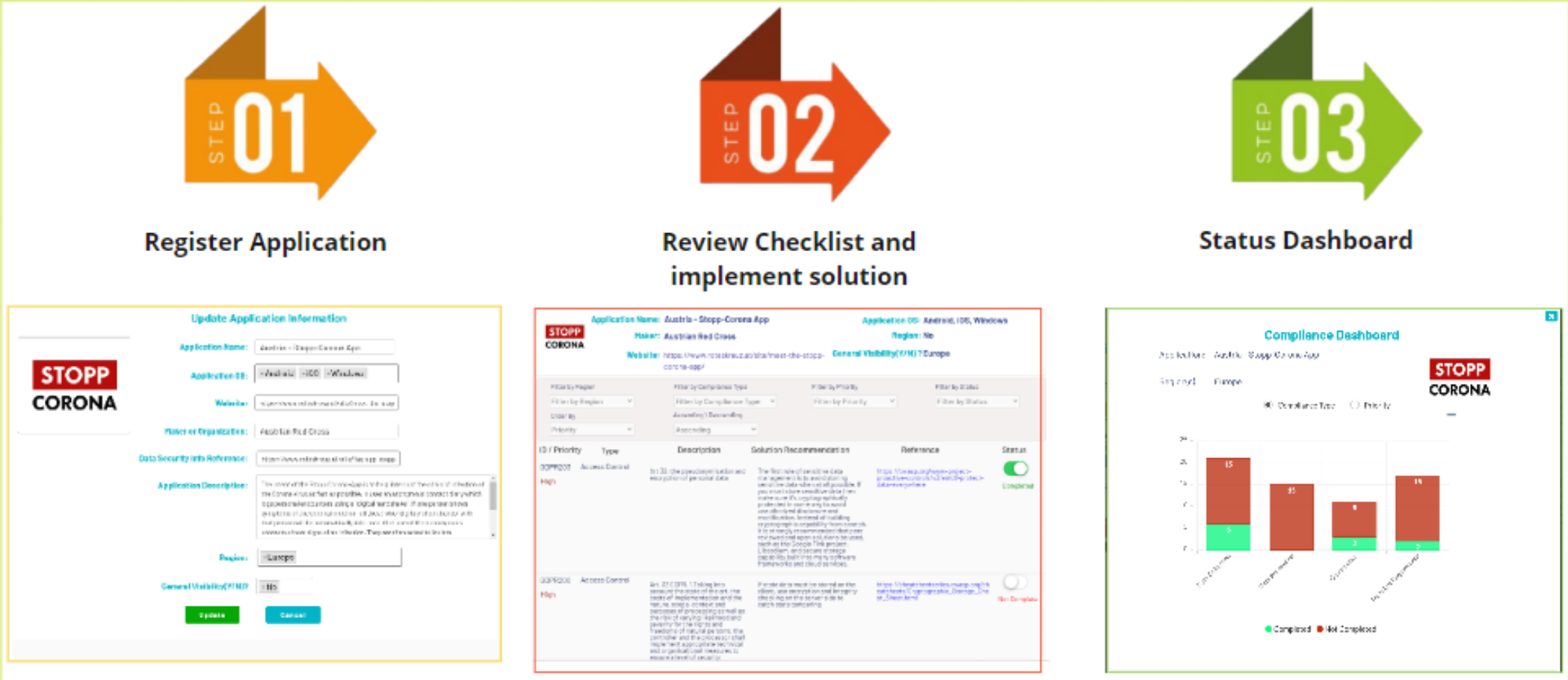
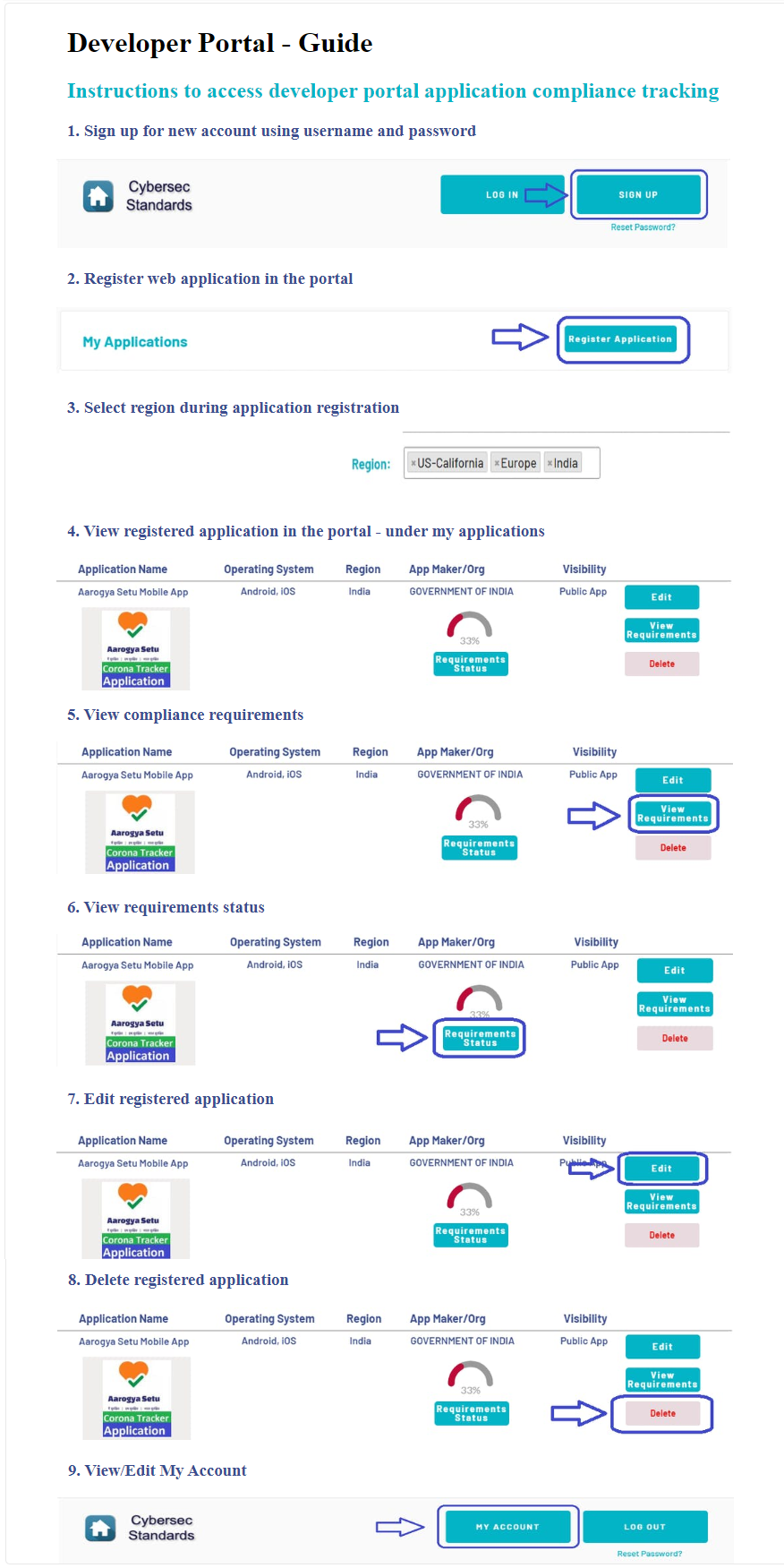
This is implemented as an interactive checklist in our developer portal.
We have also collected legal guidance and security frameworks in a MediaWiki repository.
Our capstone project was generously supported with funding from the Center for Long-Term Cybersecurity (CLTC)